Industrial automation and zero trust security

Industrial automation and zero trust are two distinct concepts, but they can intersect in the context of enhancing cybersecurity for industrial control systems (ICS) and critical infrastructure. Let’s explore each of these concepts:
- Industrial Automation: Industrial automation refers to the use of control systems such as computers or robots for handling different processes and machinery in an industry to replace human intervention. This can include manufacturing processes, machinery control, and other industrial tasks. Automation in industries often involves the use of sensors, actuators, and control systems to optimize efficiency, reduce human error, and improve overall productivity.
- Zero Trust: Zero Trust is a cybersecurity concept that assumes no entity, whether inside or outside the network, should be trusted by default. In a Zero Trust model, every user, device, or application attempting to connect to the network is treated as potentially untrusted, regardless of their location (inside or outside the corporate network). Access is only granted after verifying the identity and ensuring that the device meets security policies. Key principles of Zero Trust include:
- Verify the identity of users and devices.
- Least privilege access: Grant the minimum level of access needed for a user or device to perform its job.
- Continuous monitoring: Regularly assess and monitor the security posture of devices and users.
Integration of Industrial Automation and Zero Trust:
- Security for Industrial Control Systems (ICS): Industrial automation often involves the use of ICS to control and monitor industrial processes. These systems are critical infrastructure components and are potential targets for cyberattacks. Implementing a Zero Trust approach in the design and management of ICS helps ensure that unauthorized access is minimized, and any potential breaches are contained.
- Network Segmentation: Zero Trust often involves the concept of network segmentation, which is the division of a computer network into segments or sub-networks. In an industrial setting, network segmentation can help isolate different parts of the control system, reducing the risk of lateral movement by attackers.
- Identity and Access Management (IAM): Zero Trust relies heavily on robust IAM practices. Applying these principles to industrial automation ensures that only authorized personnel and devices have access to critical control systems. This minimizes the risk of unauthorized manipulation of industrial processes.
- Continuous Monitoring and Anomaly Detection: Continuous monitoring is a core principle of Zero Trust. In the context of industrial automation, this involves monitoring network traffic, user activities, and system behaviors to detect any unusual patterns that may indicate a security threat.
- Secure Remote Access: With the increasing trend of remote monitoring and management in industrial settings, implementing secure remote access mechanisms aligns with the Zero Trust model. This ensures that even remote connections adhere to strict security policies.
1.Need of industrial automation
what is industrial automation?
- Industrial automation is the use of robotics, machines and control systems to perform tasks that were traditionally carried out by human workers. Automation can improve productivity, quality and safety in manufacturing and other industrial applications.
- Automation technology includes a wide range of tools and technologies, such as robots, numerical control (NC) machine tools, programmable logic controllers (PLCs), computer numerical control (CNC) systems and industrial sensors. Automation systems can be integrated into existing production lines or stand-alone and can be used to collect data for preventative maintenance of the equipment.
These are few factor for need of industrial automation. They are
- Increased Efficiency: Industrial automation streamlines processes, reduces human error, and enhances operational efficiency by automating repetitive tasks and optimizing workflows.
- Cost Reduction: Automation helps lower production costs by reducing labor expenses, minimizing waste, optimizing resource utilization, and enhancing energy efficiency.
- Improved Quality Control: Automated systems can perform precise and consistent tasks, leading to higher product quality, fewer defects, and enhanced consistency in manufacturing processes.
- Enhanced Safety: Automation eliminates or reduces the need for workers to perform hazardous tasks, improving workplace safety and reducing the risk of accidents and injuries.
- Higher Production Capacity: Automated systems can operate continuously without fatigue or breaks, increasing production capacity and output levels to meet growing demand.
- Flexibility and Adaptability: Modern automation technologies offer flexibility to adapt to changing production requirements, accommodate product customization, and respond quickly to market demands.
- Data Collection and Analysis: Automation systems generate valuable data insights regarding production processes, equipment performance, and product quality, enabling data-driven decision-making and process optimization.
- Competitive Advantage: Embracing automation provides a competitive edge by enabling companies to innovate, improve productivity, shorten time-to-market, and respond more effectively to competitors and market dynamics.
2. Problem solve by industrial automation
Digital transformation is rapidly changing every industry, including the manufacturing sector. Robotics and automated machinery, as well as advanced technology like artificial intelligence (AI) and the Industrial Internet of Things (IIoT), are helping manufacturers automate business and production processes, optimize their supply chain, and improve overall efficiency.
Here are the four biggest manufacturing challenges impacting the industry, and how automation can help overcome them:
- High Material Waste
- Waste is often inevitable throughout the manufacturing process, existing in the form of scrap from defective parts, cutting fluid waste, excessive cutting tool consumption, downtime, and so much more. Automation solutions can reduce waste by streamlining production processes, optimizing material usage, and improving production quality. For example, installing machine control and data collection systems can dramatically reduce machine downtime and give manufacturers insight into production data to make better decisions.
- Rising Labor Costs
- Labor costs are one of the largest line items on every manufacturer’s budget, and they’re only growing as talent competition and the skills gap increases. The labor shortage is driving more competitive wages, while turnover is disrupting operations and forcing manufacturers to invest more in training.
- Solutions like robots and cobots can drastically offset these rising costs. Automating tasks involved in assembly, material handling, and quality control increases efficiency and can improve profit margins while minimizing reliance on labor. During busy seasons, shops can easily scale output without hiring additional support. Robots also create a more desirable workplace since they reduce manual labor required for employees.
- Better Customer Experience

- In today’s volatile marketplace, one of the biggest manufacturing challenges is simply providing satisfactory customer service. Delayed orders can be difficult to avoid with so much supply chain congestion, but customers are anxious for results and constantly looking for new, more reliable suppliers. The efficiency gains automation enables in order processing, production, and inventory management can help offset the impact of external delays and ensure smoother transactions.
- New technology can even help manufacturers improve communication and customer relations. Automation provides unprecedented visibility into the status of orders, so customers never have any doubt about where their products are or why there’s a delay. Though problems aren’t always avoidable, automation can help reduce uncertainty, providing a better experience for end users. This transparency can go a long way in improving trust and saving accounts that otherwise might have switched to competitors.
- Poor Part Quality

- Poor production processes can result in high scrap rate (increasing waste), diminished finish quality (requiring rework), and dramatically increase production costs affecting profitability. Automation can help mitigate these problems by reducing potential for human error, inconsistent processes, or improper material handling. Aside from CNC machining or 3D printing, robots can automate tasks involved in material inspection, handling, and even assembly, with greater efficiency and higher standards than manual labor. Automated sensors can also provide real-time data and analytics that help machine operators and shop managers identify quality issues early in the production process, allowing them to address problems sooner.
3.
3.Different types of cyber attacks

cyber attacks :- An attempt by hackers to damage or destroy a computer network or system.
- cyber attacks are generally classified into two types. They are
- Web-based attack
- System based attack
1) web-based attacks :-

- Injection attacks
- DNS spoofing
- Session hijacking attacks
- Phishing
- Brute force
- Denial of service
- Dictionary attacks
- URL interpretation
- File inclusion
- Man in the middle attack
- Injection attacks :- Injection attacks are a common cyberattack where an attacker injects malicious code into your web application to access your personal information or compromise your system.
- DNS spoofing :- It is a type of computer hacking, where by a data is introduced into a DNS resolvers cache causing diverting traffic to the attack computer or another computer. The DNS spoofing attacks can go on longer period of time without and being detected and can cause.
- Session hijacking attacks :- It is a security attack on a user session over a protected network. Web application create cookies to store the state and user session. By stealing the cookies, an attacker can have access to all of the users data.
- Phishing :- It is a attack which attempts to steal sensitive information like user login credential and credit number. It occurs when an attacker is masquerading as a trustworthy entity.
- Brute force :- It is an attacks which uses a trial and error method. It generates large number of guesses and validates them to passwords and pin. It is used by criminals to cracks encrypted data.
- Denial of service :- A denial of service (DoS) attack is an attack in which requests flood a server to the point that it can no longer cope with the load and crashes.
- Dictionary attacks :- Dictionary attacks are a type of cyber attack where an attacker tries to gain unauthorized access to a system or account by systematically entering a large number of words or phrases from a pre-built list, called a dictionary. This method involves trying every entry in the dictionary as a possible password or key, aiming to guess the correct one.
- URL interpretation : – URL interpretation attacks, also known as “URL parsing attacks” or “URL-based attacks,” involve manipulating the structure or content of a URL to exploit vulnerabilities in web applications. Attackers can use various techniques, such as encoding, injecting malicious code, or manipulating parameters, to deceive a system into performing unintended actions, accessing unauthorized data, or executing malicious scripts.
- File inclusion :- A file inclusion attack is a type of cyber attack that exploits vulnerabilities in a web application to execute malicious code by including files that are not intended to be accessed.
- Man in the middle attack :- If a third party manages to insert themselves between your device and the web site/application you’re connected to, you’ve just fallen victim to a “man in the middle” attack.
2) System-based attacks :-

- Virus
- Worm
- Trojan
- Backdoor
- Bots A bot attack
- Virus :- It is a type of software program that spread throughout computer files without the knowledge of a user. The computer program that replicates by inserting copies of itself into the other computer.
- Worm :- It is a type of malware function is to spread to uninfected computer it originates from email attachments appear to be from trusted senders. It work same as virus.
- Trojan horse :- It is a malicious program that occurs unexpected changes to computer setting and unusual activity, even when the computer should be idle.
- Backdoor :- It is a method that bypasses the normal authentication process. A developer may create a backdoor so that an application or operating system can be accessed by troubleshooting or other purposes.
- Bots A bot (short for “robot”) :- It is an automated process that interacts with other network services. Some bot programs run automatically while other only execute commands when they received specific input.
4. Zero trust security
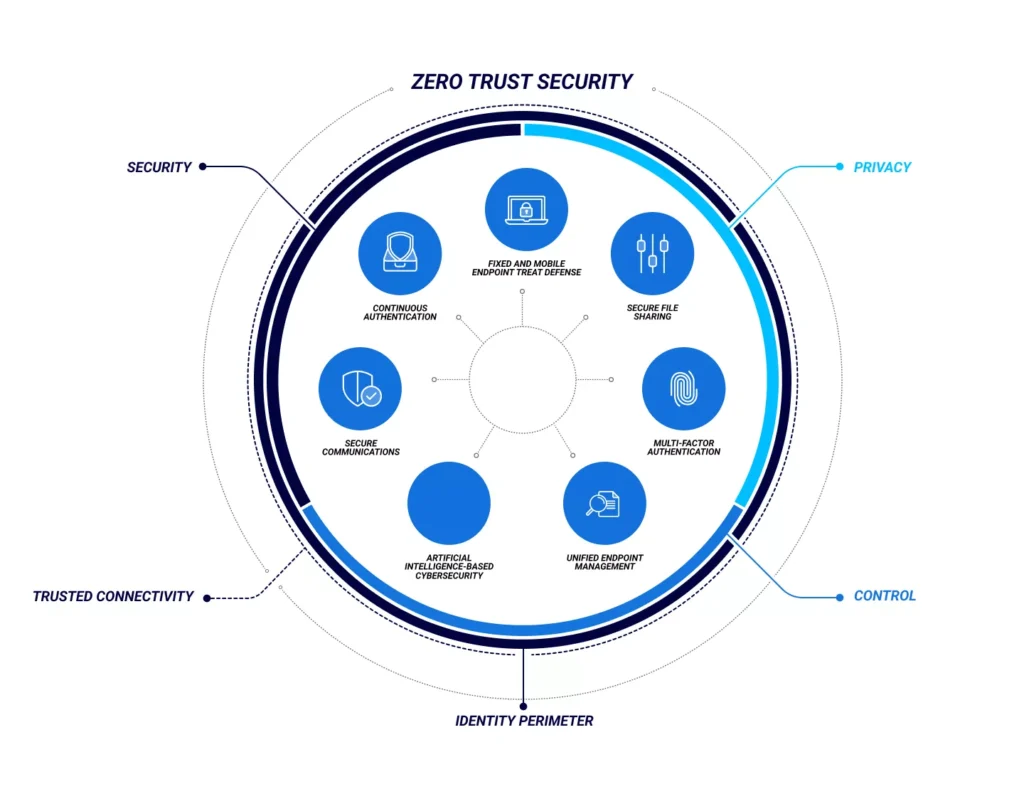
Zero Trust: Zero Trust is a cybersecurity concept that assumes no entity, whether inside or outside the network, should be trusted by default. In a Zero Trust model, every user, device, or application attempting to connect to the network is treated as potentially untrusted, regardless of their location (inside or outside the corporate network).
- Instead of assuming everything behind the corporate firewall is safe, the Zero Trust model assumes breach and verifies each request as though it originates from an open network. Regardless of where the request originates or what resource it accesses, Zero Trust teaches us to “never trust, always verify.” Every access request is fully authenticated, authorized, and encrypted before granting access. Micro segmentation and least-privilege access principles are applied to minimize lateral movement. Rich intelligence and analytics are utilized to detect and respond to anomalies in real time.
- Access is only granted after verifying the identity and ensuring that the device meets security policies. Key principles of Zero Trust include:
Zero Trust principles :
- Verify explicitly : Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
- Use least-privilege access : Limit user access with just-in-time and just-enough access (JIT/JEA), risk-based adaptive polices, and data protection to help secure both data and productivity.
- Assume breach : Minimize blast radius and segment access. Verify end-to-end encryption and use analytics to get visibility, drive threat detection, and improve defenses.
Zero Trust architecture :

About Diagram :
- A holistic approach to Zero Trust should extend to your entire digital estate—inclusive of identities, endpoints, network, data, apps, and infrastructure. Zero Trust architecture serves as a comprehensive end-to-end strategy and requires integration across the elements.
- The foundation of Zero Trust security is identities. Both human and non-human identities need strong authorization, connecting from either personal or corporate endpoints with compliant devices, requesting access based on strong policies grounded in Zero Trust principles of explicit verification, least-privilege access, and assumed breach.
- As a unified policy enforcement, the Zero Trust policy intercepts the request, explicitly verifies signals from all six foundational elements based on policy configuration, and enforces least-privilege access. Signals include the role of the user, location, device compliance, data sensitivity, and application sensitivity. In addition to telemetry and state information, the risk assessment from threat protection feeds into the policy engine to automatically respond to threats in real time. Policy is enforced at the time of access and continuously evaluated throughout the session.
- This policy is further enhanced by policy optimization. Governance and compliance are critical to a strong Zero Trust implementation. Security posture assessment and productivity optimization are necessary to measure the telemetry throughout the services and systems.
- The telemetry and analytics feeds into the threat protection system. Large amounts of telemetry and analytics enriched by threat intelligence generates high-quality risk assessments that can be either manually investigated or automated. Attacks happen at cloud speed and, because humans can’t react quickly enough or sift through all the risks, your defense systems must also act at cloud speed. The risk assessment feeds into the policy engine for real-time automated threat protection and additional manual investigation if needed.
- Traffic filtering and segmentation is applied to the evaluation and enforcement from the Zero Trust policy before access is granted to any public or private network.
- Data classification, labeling, and encryption should be applied to emails, documents, and structured data. Access to apps should be adaptive, whether SaaS or on-premises. Runtime control is applied to infrastructure with serverless, containers, IaaS, PaaS, and internal sites with just-in-time (JIT) and version controls actively engaged.
- Finally, telemetry, analytics, and assessment from the network, data, apps, and infrastructure are fed back into the policy optimization and threat protection systems.
5.Why we need zero trust security in industrial automation

- Today’s organizations need a new security model that more effectively adapts to the complexity of the modern environment, embraces the hybrid workplace, and protects people, devices, apps, and data wherever they’re located.
- Zero trust security in industrial automation is crucial for several reasons:
- Protection Against Cyber Threats: Industrial automation systems, including SCADA (Supervisory Control and Data Acquisition) systems, are increasingly becoming targets for cyber attacks. These attacks can disrupt operations, cause damage to equipment, and even endanger human lives. Zero trust security helps to mitigate these risks by assuming that threats may already exist within the network and by verifying every request for authentication and authorization.
- Complex Network Environments: Industrial automation environments often consist of complex networks that include various interconnected devices, sensors, controllers, and software systems. These networks are not always easy to monitor and secure effectively using traditional security measures. Zero trust security provides a framework for continuously monitoring and controlling access to resources, regardless of the location or status of the user or device.
- Protection of Critical Assets: Many industrial automation systems control critical infrastructure such as power plants, water treatment facilities, and manufacturing plants. Breaches in these systems can have severe consequences for public safety, the environment, and the economy. Zero trust security helps to protect these critical assets by enforcing strict access controls and continuously monitoring for suspicious activity.
- Compliance Requirements: Industries that utilize industrial automation systems are often subject to strict regulatory requirements concerning data protection and cybersecurity. Implementing zero trust security measures can help organizations demonstrate compliance with these regulations by providing a systematic approach to securing sensitive information and critical infrastructure.
- Adaptation to Modern Threat Landscape: The traditional perimeter-based security model, which assumes that threats are outside the network, is no longer sufficient in today’s threat landscape where attacks can originate from both internal and external sources. Zero trust security, which is based on the principle of “never trust, always verify,” is better suited to address the evolving nature of cyber threats by focusing on protecting individual resources and enforcing least privilege access controls.

